When you're serious about holding crypto, the first and most important step is moving it off an exchange. Think of it this way: keeping your assets on a trading platform is like leaving cash at a busy public kiosk. True security means taking it home and putting it in your own vault—a personal wallet where you, and only you, control the private keys.
For anyone planning to hold for the long term, a hardware wallet is the undisputed champion. It takes your keys completely offline, walling them off from the endless barrage of online threats like sophisticated hacks and sneaky malware. It’s a simple move that makes a world of difference.
The High Stakes of Crypto Security
The crypto world is thrilling, no doubt, but it's a wild frontier. Security isn't just a nice-to-have feature; it's the bedrock of your entire investment. Forget what you know about traditional banking. There are no fraud hotlines to call, no chargebacks, and no way to undo a transaction sent to the wrong address or siphoned off by a scammer.
Once your crypto is gone, it's almost certainly gone forever. This is the stark reality that makes mastering secure storage a non-negotiable skill for every single person in this space.
The risks aren't just hypotheticals. Digital asset theft is a booming industry for criminals. So far this year, a staggering $2.17 billion has been snatched from crypto platforms in the first half alone. At this rate, the total could blow past $4.3 billion by the end of the year.
The pace is picking up, too. In 2022, it took 214 days for thieves to hit the $2 billion mark. This year? They did it in just 142 days. You can dig into the unsettling details and get more insights from the full report on these crypto crime trends.
Your Path to a Secure Setup
This guide is your roadmap. We’re cutting through the jargon to give you clear, practical steps to build a fortress around your assets. We're not just going to tell you what to do; we're going to explain why it's so critical.
Here’s a look at what’s ahead:
- Hot vs. Cold Wallets: We'll break down the fundamental difference between online ("hot") and offline ("cold") storage, so you can pick the right tool for the job.
- Hardware Wallet Mastery: Consider this your personal walkthrough for setting up and using a hardware wallet, the gold standard for keeping your crypto safe.
- Bulletproof Recovery Plan: You'll learn how to create a backup system for your recovery phrase that’s tough enough to withstand anything, ensuring you never lose access to your funds.
The most important rule in crypto is simple: "Not your keys, not your coins." If you don't hold the private keys, you're just trusting someone else to hold your money for you. That introduces risks you have zero control over.
Our mission is to arm you with the confidence and know-how to take full ownership of your digital wealth. As a leader in commission-free trading, we at vTrader firmly believe that an educated investor is a successful one. That’s why we’re committed to providing this essential security training—you can learn more about our philosophy here.
By the time you're done with this guide, you'll have a complete framework for securing your cryptocurrency for the long haul.
Choosing Your Storage: Hot vs Cold Wallets
Every crypto owner hits a fork in the road sooner or later: picking the right wallet. This decision is the bedrock of keeping your crypto safe. Think of it like your bank accounts—you've got a checking account for daily coffee runs and a high-security vault for your life savings. That's the hot vs. cold wallet debate in a nutshell.
A hot wallet is your crypto checking account. It's connected to the internet, always ready for action. Whether you're trading on an exchange, snagging an NFT, or diving into DeFi, it's your go-to for quick transactions. But that constant online connection, while super convenient, also leaves it exposed to hackers and scams.
On the flip side, a cold wallet is your personal Fort Knox. It lives completely offline, meaning your private keys—the only way to access your funds—are never touched by the internet. This "air-gapped" approach makes them practically bulletproof against remote hacking, phishing, and malware.
The Tradeoff Between Access and Security
The choice really boils down to convenience versus security. Hot wallets are fast and easy, but that very accessibility is their biggest weakness.
The numbers don't lie. Hot wallets make up a staggering 78% of all wallets used globally, mostly because they're so easy to use for everyday activity. However, this comes at a steep price, with over $1.1 billion in wallet-related thefts this year alone directly tied to their online vulnerabilities. In contrast, cold wallets account for the other 22% and are quickly becoming the standard for serious, long-term investors—their sales have jumped by 31% this year.
This doesn't mean hot wallets are bad. They're a crucial tool, but you have to be smart about how you use them.
- For Daily Use: Treat it like pocket money. Only keep a small amount of crypto in a hot wallet that you're okay with potentially losing.
- For Long-Term Holdings: Your serious investments—the crypto you plan to hold for months or years—belongs in the airtight security of a cold wallet.
Custodial vs Non-Custodial Wallets
Beyond the hot/cold debate is another crucial layer: who actually holds the keys.
A custodial wallet is when a third party, like a crypto exchange, manages your private keys for you. It's simple, especially for beginners, but it's a huge leap of faith. You're trusting that company with your money, making you vulnerable if they get hacked, go bust, or decide to freeze your account. This is where the old crypto saying comes from:
"Not your keys, not your coins." If you don't control the private keys, you're just trusting someone else to hold your money for you.
A non-custodial wallet, however, puts you in complete control. You hold your own private keys, whether it's on a software app or a hardware device. You are your own bank. This gives you total ownership over your assets, but it also means security is 100% your responsibility.
This is a classic hardware wallet, the gold standard for non-custodial cold storage.
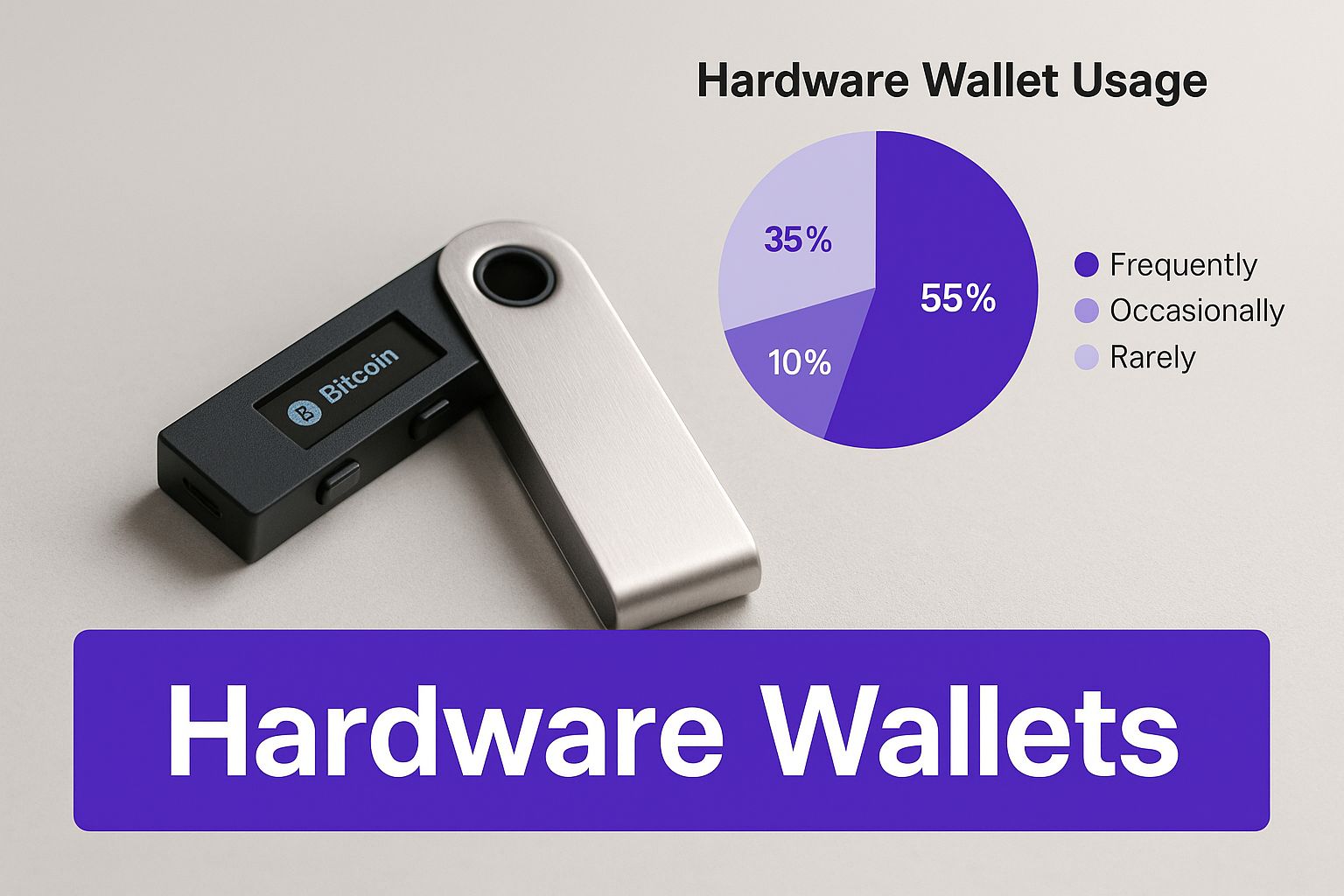
The device itself highlights the physical nature of top-tier crypto security—your keys are stored on a dedicated piece of hardware that never connects to the open internet.
Hot Wallet vs Cold Wallet At a Glance
Still on the fence? This quick comparison breaks down the key differences to help you decide which wallet type fits your needs.
| Feature | Hot Wallet (Online) | Cold Wallet (Offline) |
|---|---|---|
| Connectivity | Always connected to the internet | Completely offline; "air-gapped" |
| Security | Vulnerable to online threats (hacks, malware) | Highly secure; immune to remote attacks |
| Convenience | High; ideal for frequent trading and transactions | Lower; requires physical access for transactions |
| Best For | Small amounts, daily spending, active traders | Large amounts, long-term holding ("HODLing") |
| Example | Exchange wallets, mobile apps (MetaMask) | Hardware wallets (Ledger, Trezor), paper wallets |
Ultimately, the best approach uses a bit of both. You get the convenience of a hot wallet for active use while keeping the bulk of your assets safe in a cold wallet.
Making the Right Choice for You
So, what's the verdict? For most people, a hybrid strategy is the smartest way to go, playing to the strengths of each wallet type. Use a hot wallet for active trading and DeFi, but keep your main portfolio locked down in cold storage. And when you are trading, don't forget about the costs involved; take a look at our guide on understanding crypto trading fees to make sure you're not leaving money on the table.
Here’s what a balanced, practical setup looks like:
- Exchange Wallet (Custodial, Hot): Perfect for buying crypto with dollars and for making quick, short-term trades. Only keep what you need for your immediate moves here.
- Software Wallet (Non-Custodial, Hot): A mobile or desktop wallet like MetaMask is great for interacting with dApps or managing smaller amounts you need ready access to.
- Hardware Wallet (Non-Custodial, Cold): This is the vault for your “HODL” stack—the majority of your crypto that you’re in for the long haul.
By splitting your funds this way, you dramatically reduce your risk. If your hot wallet ever gets compromised, the damage is contained to a small, manageable portion of your portfolio, while your main savings remain untouched and secure in cold storage.
A Practical Guide to Hardware Wallets
If you've decided to take full control of your crypto, a hardware wallet is your best ally. Think of it as a specialized, highly secure USB drive built for one thing only: to keep your private keys completely isolated from the internet. This physical barrier is what makes it the gold standard for anyone serious about securing their digital assets long-term.
When you use a hardware wallet, every transaction you make has to be physically confirmed on the device itself. This is a game-changer. Even if your computer is riddled with malware, a hacker can't drain your funds because they can't reach over and press the buttons on your device. It creates a powerful "air gap" between your keys and online threats.
Preventing crypto theft and scam losses really comes down to robust storage methods and being vigilant. Devices like the Ledger Nano X or Trezor are designed to isolate your private keys from anything connected to the internet, dramatically cutting your risk of getting cleaned out by a hack. Even with a compromised computer, your funds are safe unless you get tricked into signing a malicious transaction. You can get more insights on the state of crypto scams at Ledger.com.
Setting Up Your First Hardware Wallet
Getting started with a hardware wallet can feel a little intimidating, but modern devices have made the whole process remarkably simple. The absolute most important part is following the instructions with intense focus. Don't skim.
Here's a general idea of what to expect when you set up a device like a Ledger or Trezor for the first time.
-
Purchase from an Official Source: This is non-negotiable. Never buy a hardware wallet from a third-party marketplace like eBay or a secondhand seller. Scammers are known to pre-configure these devices to steal your crypto the moment you deposit it. Always buy directly from the manufacturer’s official website.
-
Initial Device Setup: Once you unbox it, you'll plug it into your computer and follow the on-screen prompts. This usually starts with setting a PIN code, which is your first line of defense against someone getting physical access to your wallet if it's ever lost or stolen.
-
Generating Your Recovery Phrase: Next, the device will generate a 24-word recovery phrase, sometimes called a seed phrase. This is the single most important piece of information you will ever handle in your crypto journey. This phrase is the master key to all your funds.
Your hardware wallet can be lost, stolen, or smashed to bits, and it won't matter—as long as you have your recovery phrase. With it, you can buy a new device from any compatible brand and restore full access to your crypto. Without it, your funds are gone forever.
Securing Your Recovery Phrase
Writing down your recovery phrase is a moment that demands your full attention. Your entire crypto portfolio rests on how well you protect these 24 words.
Do not, under any circumstances, store your recovery phrase digitally. That means no photos on your phone, no text files on your computer, and absolutely no saving it in a cloud drive or password manager. Any digital copy is a juicy target for hackers.
So, how should you store it?
-
The Paper Method (Good): Your wallet will come with a card to write your phrase on. This is a solid starting point, but let's be honest, paper is fragile. It can be easily destroyed by fire, water, or just fade over time. If you use paper, make multiple copies and store them in separate, secure physical locations.
-
The Steel Plate Method (Better): For much better durability, look into a steel wallet or metal seed storage device. These are engineered to be fireproof, waterproof, and corrosion-resistant. You typically stamp or engrave your seed phrase onto metal plates, creating a backup that can survive almost anything.
Performing a Security Check
Once your phrase is safely stored, it’s time for a crucial final check before you move your life savings over. A great practice is to send a tiny, test amount of crypto to your new hardware wallet address.
After you confirm the deposit has arrived, intentionally wipe the hardware wallet. Then, use your newly recorded recovery phrase to restore it from scratch. If your test funds reappear, you've confirmed two critical things: your device works perfectly, and more importantly, you recorded your recovery phrase 100% correctly. This small step provides immense peace of mind.
Building Your Digital Security Habits

Here’s the hard truth: even the most sophisticated hardware wallet is useless if your personal security habits are sloppy. Technology gives you the tools, but your daily actions are what really stand between your crypto and the thieves trying to get it. Poor practices can completely undermine the best defenses, making you the weakest link in your own financial security.
This is where the human element becomes critical. You need to build a strong security mindset, treating every online interaction with a healthy dose of skepticism. It's about embedding good practices into your routine until they're second nature, transforming yourself from a potential target into a hardened defender of your assets.
Fortifying Your Digital Life
First things first, lock down your entire digital identity. Your passwords and authentication methods are the keys to the kingdom, and they need to be treated as such. Using weak or recycled passwords is like leaving your front door wide open.
You absolutely need a reputable password manager. It’s non-negotiable. These tools generate long, complex, unique passwords for every site you use and store them securely. This single change demolishes the huge risk of a data breach on one site exposing all your other accounts.
Next up is Two-Factor Authentication (2FA). Enable it everywhere you can. This adds a critical second layer of defense, demanding a code from your phone or another device before granting access.
- Authenticator Apps: Ditch SMS-based 2FA. Hackers can use "SIM swap" attacks to hijack your phone number and intercept those text message codes. Instead, use an app like Google Authenticator or Authy, which generate secure codes locally on your device.
- Hardware Security Keys: For maximum-security accounts—like your primary email—get a physical security key like a YubiKey. You have to physically plug it in and touch it to log in, making it virtually impossible for a remote attacker to get past it.
Recognizing and Dodging Phishing Attacks
Phishing is still one of the most effective tricks in a crypto thief's playbook. These scams are cleverly designed to trick you into giving up your login details or, in the worst-case scenario, your private recovery phrase. They almost always play on a sense of urgency, fear, or greed.
A classic example is an email that looks like it's from your exchange, screaming about an "unauthorized login attempt." It will push you to click a link to secure your account immediately. Of course, that link leads to a perfect replica of the exchange's website, built for one purpose: to steal your credentials.
Phishing isn't just in your inbox anymore. Scammers are all over social media DMs, posing as fake support agents on Discord and Telegram, and even running malicious ads in search results. The playbook is always the same: create panic to make you act before you think.
Here’s how you spot these traps:
- Check the Sender: Look very closely at the sender's email address. Scammers will often use addresses that are just one character off, like
support@coinbse.cominstead ofsupport@coinbase.com. - Hover Before You Click: Always hover your mouse over a link before clicking. Your browser will show the actual destination URL in the bottom corner. If it doesn't match the legitimate website's domain, it's a trap.
- Look for Urgency: Be instantly suspicious of any message that demands immediate action or threatens to suspend your account. This is a psychological trick designed to make you panic and make a mistake.
Staying on top of the latest threats is half the battle. You can track breaking stories and security alerts in our crypto news hub to stay a step ahead.
Ultimately, knowing how to store cryptocurrency safely is as much about your behavior as it is about the wallet you choose.
Developing a Bulletproof Recovery Plan

Owning a top-tier hardware wallet is a great start, but let's be honest—it's only half the battle. Your setup could be Fort Knox on a chip, but it means nothing if you don't have a solid plan for when life happens.
What if your device gets lost in a move, stolen, or destroyed in a house fire? Your crypto isn't gone, but your access to it might be. That is unless you've built a robust recovery plan.
This is about more than just scribbling down your recovery phrase. It's about engineering a system that ensures you, and only you, can get back to your funds, no matter what. The entire resilience of your portfolio hangs on the strength of this plan.
Beyond Simple Pen and Paper
When you set up a new wallet, you get a recovery phrase, usually 12 or 24 words long. Writing it on the little paper card they give you is step one, but it absolutely cannot be the last. Paper is fragile. It hates water, burns easily, and simply falls apart over time. For long-term security, you have to think bigger.
A serious upgrade is a metal seed storage solution. These devices are purpose-built to be fireproof, waterproof, and crushproof. You physically stamp or engrave your phrase into steel plates, creating a backup that can literally survive a catastrophe. It's a one-time cost for some serious peace of mind.
Think of your recovery phrase as the master key to your digital wealth. It deserves the same level of seriousness as the deed to your house.
Protecting it from physical damage is one thing, but you also need a strategy to keep it away from prying eyes. This is where location and access control come into play.
Designing Your Recovery Strategy
A single, well-protected backup is good. A distributed, redundant system is far better. The name of the game is eliminating any single point of failure. You never want one unlucky event—a burglary, a flood—to be the reason you lose access forever.
A smart approach is geographic distribution, which just means storing copies of your recovery phrase in two or more separate, secure locations.
- A fireproof safe at home.
- A safe deposit box at your bank.
- The home of a trusted family member who lives in another city.
By spreading them out, you make sure that a disaster in one location doesn't take out your only path to recovery.
Another slick technique is splitting the phrase. Instead of storing the full 24-word phrase in one spot, you break it into pieces. You could store words 1-12 in one location and words 13-24 in another. A thief would need to compromise both locations to get the full key, adding a powerful layer of security.
Introducing Advanced Security with Multisig
For those with significant holdings or who need institutional-grade security, a multi-signature (multisig) wallet is the logical next step. Imagine a bank vault that needs two different keys turned at the same time to open.
A multisig wallet requires multiple private keys to approve a transaction. A very common setup is "2-of-3," where you create three separate keys, but only two are needed to sign off on sending funds. This structure provides incredible protection against both theft and simple human error.
- Key 1: Kept on your main computer.
- Key 2: Stored on your hardware wallet.
- Key 3: Engraved on a metal plate in a secure, offsite location.
In this scenario, a hacker who gets into your computer is still stuck—they can't move your funds. If you lose your hardware wallet, you're still in control with the other two keys. This approach builds security and redundancy directly into your wallet's DNA, making it incredibly tough to crack.
Of course, using advanced tools often comes with specific platform rules. You can always review the terms and conditions of service to see how features like these are managed.
Common Questions About Storing Crypto
Diving into crypto security always brings up a host of questions. As you get the hang of storing your cryptocurrency safely, you’ll find certain concerns pop up over and over again. Let’s tackle some of the most common ones head-on with practical answers to help you lock down your digital assets.
Is It Safe to Keep Crypto on an Exchange
While exchanges like Coinbase or Binance are undeniably convenient for quick trades, leaving large amounts of crypto there long-term is a gamble. The moment your assets are on an exchange, you’re not the one in control of the private keys—the exchange is. This is what’s known as custodial storage.
This setup leaves you vulnerable to massive risks you can’t control, like a major exchange hack, a sudden bankruptcy filing, or having your account frozen without warning. There’s a powerful saying in the crypto world for a good reason.
"Not your keys, not your coins."
This mantra is the bedrock of self-sovereignty in the crypto space. For any serious amount of capital, the smartest move is always to transfer your funds to a non-custodial wallet where you, and only you, hold the keys.
What Happens If I Lose My Hardware Wallet
This is a fear that trips up a lot of newcomers, but the answer really showcases the genius behind hardware wallet technology. If your device gets lost, stolen, or even smashed to bits, your crypto is completely safe—as long as you have your recovery phrase.
Your assets never actually live on the device itself; they exist on the blockchain. The wallet is just a highly secure key that grants you access. You can simply grab a new hardware wallet (even from a different brand), punch in your recovery phrase during the setup, and you'll regain full access to all your funds. This is exactly why safeguarding that phrase is your number one job.
Is Writing My Recovery Phrase on Paper Good Enough
Jotting down your recovery phrase on a piece of paper is a solid first step, but it’s far from a bulletproof solution. Think about it: paper is incredibly fragile. It's easily destroyed by common household accidents like a fire or a flood, not to mention it can simply degrade over time.
For genuine, long-term security, it’s worth investing in a metal seed storage device. These things are built like tanks, designed to survive extreme conditions and ensure your master key makes it through anything.
Crucially, never store your recovery phrase digitally. Don't take a photo of it, don't save it in a text file, and definitely don't upload it to a cloud service. A digital copy is a neon sign for hackers. If you're looking for more answers, you can dig into this extensive FAQ on crypto trading and security.
What Is a Multisig Wallet and Do I Need One
A multi-signature wallet, or multisig, adds a serious layer of security by requiring more than one key to sign off on a transaction. It’s like a bank’s safe deposit box that needs two different keys turned at the same time to open.
A popular configuration is a "2-of-3" setup. Here, three unique keys are created, but any two of them can authorize a transaction. This creates redundancy and protects you from a single point of failure. If one key is lost or compromised, your funds are still locked down and secure. Multisig is definitely an advanced strategy, usually best for businesses or individuals holding significant assets who need that next level of protection.
At vTrader, we believe that a secure investor is a successful one. Start your journey with a platform that prioritizes your safety and offers zero-fee trading to maximize your potential. Join us today and build your portfolio with confidence at https://www.vtrader.io.

Steve Gregory is a lawyer in the United States who specializes in licensing for cryptocurrency companies and products. Steve began his career as an attorney in 2015 but made the switch to working in cryptocurrency full time shortly after joining the original team at Gemini Trust Company, an early cryptocurrency exchange based in New York City. Steve then joined CEX.io and was able to launch their regulated US-based cryptocurrency. Steve then went on to become the CEO at currency.com when he ran for four years and was able to lead currency.com to being fully acquired in 2025.


