Staying safe from phishing isn’t about one magic bullet. It’s a combination of healthy skepticism, locking down your accounts, and just being aware. The best defense is a practical one: learn to spot the scams, then use the right tools—like two-factor authentication—to build a wall scammers can't climb.
This approach hardens your digital life against fraudsters.
Understanding the Phishing Threat Landscape

Forget those old, terribly-written emails from a supposed foreign prince. Today’s phishing attacks are slick, personal, and shockingly convincing. They’re designed to manipulate our natural human instincts—trust, curiosity, or a sudden sense of panic—to trick us into handing over the keys.
These attacks come from all angles, from text messages (smishing) to direct phone calls (vishing).
The goal, however, is always the same: steal your sensitive information. That could be anything from login credentials and credit card numbers to personal data they can use for identity theft. In the crypto world, a single successful phish can mean your assets are gone forever, with no bank to call for a refund. It all comes down to protecting your private key; after all, understanding the difference between a https://www.vtrader.io/news/public-key-vs-private-key/ is what separates a safe investor from a victim.
Core Pillars of Phishing Defense
To keep things simple and actionable, we're focusing on three core areas. Master these, and you'll have a robust defense against nearly any phishing attempt that comes your way.
Here’s a quick overview of what we'll cover to help you build a comprehensive defense.
Core Pillars of Phishing Defense
| Strategy Pillar | Primary Action | Why It Matters |
|---|---|---|
| Awareness & Identification | Train your eye to spot red flags in emails, texts, and websites. | This is your first line of defense. Spotting a fake before you click is the ultimate win. |
| Technical Hardening | Secure your accounts with strong passwords, 2FA, and browser tools. | This creates a technological barrier that stops scammers even if you make a mistake. |
| Incident Response | Know exactly what to do when you encounter a suspicious message or click a bad link. | A fast, smart response can neutralize a threat and prevent or minimize damage. |
This framework covers all the bases—from your own intuition to the tech that backs you up.
By building skills in each of these pillars, you create a security posture that’s tough to break. If you're looking for an even more in-depth look, check out our detailed guide on practical steps to protect against phishing attacks.
Let's get started.
How to Spot a Phishing Attack in the Wild

Knowing what phishing is in theory is one thing; spotting a clever fake in your own inbox is another game entirely. Scammers are master manipulators, playing on our built-in trust for familiar brands and our fear of losing access to our accounts.
The single most effective defense is to just slow down. Scammers want you to act fast, without thinking. By taking a few extra seconds to actually look at the messages you receive, you can spot the subtle mistakes that even the most convincing fakes almost always contain.
Deconstructing the Phishing Email
Email is still the number one playground for phishers. The FBI’s Internet Crime Complaint Center (IC3) fields nearly 300,000 complaints about it in a single year. Attackers love to pose as giants like Amazon, Microsoft, or your bank because that credibility does half the work for them.
Before you even think about clicking a link or opening a file, it's time to put on your detective hat.
- Check the Sender's Address: Don't just glance at the display name that says "PayPal Support." Look at the actual email address. Is it from a legitimate domain? Scammers use lookalikes like
support@paypa1.com(using a 1 instead of an L) or weird, long addresses likesecurity-alert-8371@mail-hosting-24.net. - Look at the Greeting: Real companies you do business with will use your name. If you see a generic opener like "Dear Valued Customer" or "Hello User," your alarm bells should be ringing.
- Hover Before You Click: This is the most critical step. Rest your mouse cursor over any link in the email, but don't click it. A little box will pop up showing the link’s true destination. If the email claims to be from Netflix but the link points to
bit.ly/random-stringor something sketchy likenetfIix-secure-logins.info, you've caught a phish. - Spot the Scare Tactics: Phishing thrives on panic. They use urgent, threatening language to bypass your rational brain. Watch out for phrases like "Your account will be suspended," "Suspicious activity detected," or "Immediate action required." It’s a classic con.
Real-World Email Phishing Examples
Let’s walk through a couple of common traps you’ll almost certainly encounter.
Example 1: The Fake Invoice
An email lands in your inbox from "Geek Squad" with a PDF invoice attached for a $399.99 auto-renewal you don't remember. The message urges you to call their support number immediately to cancel and get a refund.
- The Trap: The PDF itself might be clean, but the phone number is the real weapon. It connects you to a scammer who will pose as support, ask for remote access to your computer to "process the refund," and then drain your bank accounts.
Example 2: The Password Reset Alert
You get an official-looking email from the "Microsoft Account Team" warning you that someone from another country tried to access your account. Helpfully, there's a big button to "Reset Your Password Now."
- The Trap: That button leads to a pixel-perfect clone of the real Microsoft login page. When you type in your current password and your "new" one, you’re just handing the keys over to the attacker.
Pro Tip: Never, ever use links in an email to log into a sensitive account. Always open a new browser tab and type the website's address (like
outlook.comorchase.com) yourself. This ensures you're on the real site, not a fake.
Smishing and Social Media Scams
Phishing isn't just an email problem anymore. Smishing (phishing via SMS) and scams sent through social media direct messages (DMs) are exploding because they feel more personal and urgent.
The tactics are the same, just condensed for a smaller screen.
- Package Delivery Scams: A text from an unknown number says a package for you is on hold due to a small, unpaid customs fee. It provides a short link to "track your delivery" or "settle the payment."
- "You've Won!" Messages: You get a DM on Instagram from an account impersonating a big brand or celebrity. They say you've won a giveaway and just need to click a link and enter your details to claim your prize.
- Crypto-Specific Lures: Scammers are incredibly active in the crypto world. They might send a fake alert from what looks like a major exchange, warning of an unauthorized withdrawal. Their goal is to panic you into clicking a link to their fake login page and steal your credentials. Protecting these assets is a unique challenge; you can get up to speed with our guide on crypto security basics.
At the end of the day, it doesn't matter if it's an email, text, or DM—the scammer's playbook is the same. Skepticism, link inspection, and questioning urgency are your best defenses. To really sharpen this skill, it's worth diving into some expert advice on how to identify phishing emails. It’s one of the most powerful tools you have to protect yourself.
Building a Fortress Around Your Digital Life

Being able to spot a phishing attempt is a critical skill, but let's be realistic—relying on vigilance alone is a recipe for disaster. Even the most seasoned expert can get tricked on a busy or distracted day. This is why building strong, technical defenses around your accounts isn't just a good idea; it's non-negotiable.
Think of it like locking your front door at night. You're not paranoid; you're just taking a practical step to secure your home. We're going to apply that same common-sense logic to your digital life, creating barriers that stop attackers in their tracks even if they somehow manage to fool you.
Your Most Powerful Defense: Multi-Factor Authentication
If you do only one thing after reading this article, make it this: enable multi-factor authentication (MFA) on every single account that offers it. Often called two-factor authentication (2FA), it’s hands down the single most effective way to shut down account takeovers.
Here’s how it works: MFA requires a second piece of information besides your password to log in. That second "factor" is typically something only you have, like a one-time code from an authenticator app on your phone, a tap on a security key, or even your fingerprint.
So, even if a scammer tricks you into giving up your password on a fake website, they’re stopped dead. They can’t get past the second step because they don't have your phone. The data is clear on this: in 2024, a massive 80% of phishing campaigns were designed to steal credentials. Yet, organizations that enforced MFA saw account takeovers from phishing plummet by as much as 90%, according to reports from APWG.org.
Key Takeaway: Enabling MFA transforms your password from a single point of failure into just one part of your security puzzle. It's the digital equivalent of adding a deadbolt to your front door.
Beyond Bad Passwords
The days of using "Password123!" or your dog's name for every website are long gone. Attackers don't just guess passwords anymore; they use automated software to test millions of leaked credentials against your accounts in what's called credential stuffing. If you reuse passwords, a breach at some obscure forum you used years ago can give a hacker the keys to your email, bank, and crypto accounts.
The solution is a password manager. These tools are essential. They generate incredibly complex and unique passwords for every site, store them securely, and fill them in for you.
- Generation: They create random passwords like
k&9^z#T@eF7!pL*qthat are impossible for a human to guess and a nightmare for a computer to crack. - Storage: All your passwords live in an encrypted vault, protected by one strong master password that only you know.
- Auto-fill: Most integrate with your browser, automatically filling in login details. This is a huge security benefit—it prevents you from accidentally typing your password into a convincing-looking phishing site.
Top choices include Bitwarden, 1Password, and LastPass. Using one removes the mental burden of juggling dozens of unique passwords and massively boosts your security. This is especially crucial when it comes to crypto, and you can learn more in our dedicated guide on how to secure your crypto wallet: https://www.vtrader.io/news/how-to-secure-your-crypto-wallet-2/
Smart Browser and App Habits
Your web browser and mobile apps are your gateways to the internet, and a few simple tweaks can make them much safer. Keeping them updated is the bare minimum, as updates often contain critical security patches that close vulnerabilities attackers love to exploit.
Beyond that, it's about practicing good digital hygiene.
- Review App Permissions: Seriously, take a look at your phone. Does that game really need access to your contacts and microphone? Regularly audit these permissions in your settings and revoke access for any app that doesn't absolutely need it.
- Limit Browser Extensions: Extensions can be super useful, but each one is also a potential security risk. Stick to extensions from reputable developers and uninstall any you aren't actively using.
- Use Secure Connections: Always look for the padlock icon in your browser's address bar, which indicates an HTTPS connection. This encrypts the data between you and the website, making it unreadable to anyone snooping on a public Wi-Fi network.
These small, consistent habits reinforce your defenses, closing the backdoors that phishers often rely on to sneak past your main security.
Using Automated Tools for Advanced Defense
Staying vigilant is your first and best defense, but trying to manually fight off every phishing attempt is a losing battle. It’s exhausting. Technology can be your 24/7 digital bodyguard, catching sophisticated threats before they ever hit your inbox.
This is where automated tools come into play. They build a layered security system that works around the clock, neutralizing threats at every stage—from a malicious email being sent to malware trying to execute on your machine.
The Power of AI-Powered Email Filtering
Your inbox is the primary battlefield. While providers like Gmail and Outlook have decent built-in filters, they often aren't enough. For a truly hardened defense, you need dedicated security solutions that go way beyond simple keyword filtering.
Modern systems use machine learning to analyze countless data points in real time. They check a sender's reputation, scan for hidden code in attachments, and even analyze the language of the message itself to spot the psychological tricks common in phishing scams.
With a staggering 3.4 billion phishing emails sent every day in 2025, it’s clear that old-school filters can't keep up. In fact, organizations saw a 47% jump in attacks that bypassed native defenses, proving just how necessary advanced tools are. The good news? Tools that use behavioral analysis can block up to 95% of these attempts before you ever see them.
Here’s a basic look at how these filtering systems work, acting as a gatekeeper for your inbox.
This visual shows the filter sorting legitimate mail from spam and potential threats—a fundamental process in protecting yourself from phishing.
Endpoint Protection: Your Last Line of Defense
Okay, so what happens if a clever email slips through and you accidentally click a bad link or download a compromised file? This is where endpoint protection—what most of us just call antivirus software—jumps into action.
But modern endpoint security is so much more than a simple virus scanner. It offers real-time protection by:
- Monitoring Behavior: It actively watches for suspicious activity, like a program suddenly trying to encrypt your files (the classic sign of ransomware) or another app trying to access your webcam.
- Scanning Downloads: Any file you download gets scanned for malware before it has a chance to run and cause damage.
- Web Protection: Many security suites come with browser extensions that block you from visiting known phishing sites, giving you that critical warning just before you land on a fake login page.
Think of it like a security guard posted inside the building. Even if a scammer gets past the front door, this guard is there to stop them from doing any real harm.
Pro Tip: Always keep your endpoint protection software set to update automatically. New threats pop up daily, and your software is only as good as its latest threat definitions.
Hardening Your Browser and Network
Your web browser is your window to the internet, and a few smart habits can make it a much safer one. Browsers like Chrome, Firefox, and Safari have built-in security features that warn you about sketchy sites. Make sure those are turned on.
For another powerful layer of security, especially on public Wi-Fi, use a reputable Virtual Private Network (VPN). A VPN encrypts all your internet traffic, making it gibberish to anyone trying to snoop on what you're doing. This stops attackers on the same network from stealing your data or redirecting you to phishing sites.
This is especially critical for crypto users, where security is everything. For another key layer of offline protection, nothing beats a hardware wallet. You can learn more about how they safeguard your assets in our guide on what is a hardware wallet.
Creating a Culture of Security at Work
Technology and firewalls are great, but your first and last line of defense against phishing will always be your people. Attackers know this. They aren't just targeting systems; they're targeting your team members, hoping for one wrong click. Building a true culture of security means shifting from rigid rules and penalties to empowering every single person to be a defender.
This change has to start at the top. When leadership stops treating cybersecurity as "an IT problem" and starts championing it as a shared responsibility, employees pay attention. The mission is to transform the mindset from one of fear and compliance to one of collective, proactive vigilance.
Effective Security Awareness Training
Let's be honest: nobody learns anything from those once-a-year, click-through slideshows. To build real resilience, training needs to be continuous, engaging, and directly relevant to the threats people are seeing in their inboxes right now.
The best training programs tell a story. Instead of just listing what a phishing email might look like, show them a real-world fake invoice that hit another company in your industry. Break down a sophisticated LinkedIn scam that targeted executives. Make it real.
- Interactive Modules: Ditch the long PDFs. Use short, interactive learning modules that people can do on their own time. Adding a little gamification, like quizzes or leaderboards, goes a long way.
- Regular Updates: Threats evolve weekly, not yearly. A quick five-minute update on a new SMS scam is far more valuable than a two-hour annual refresher course.
- Role-Specific Scenarios: Your finance team needs to be razor-sharp on wire transfer and invoice fraud. Your sales team, on the other hand, should be trained to spot scams coming through professional networking sites. For anyone handling crypto, it's absolutely vital to include training on exchange impersonations and fake wallet updates. You can learn more about avoiding crypto scams with these 7 red flags.
This constant drip of practical knowledge is what makes security habits stick.
The Power of Phishing Simulations
One of the most effective tools in the training arsenal is the simulated phishing campaign. This is where you send safe, controlled, fake phishing emails to your own staff to see who takes the bait.
The goal here isn't to shame anyone who clicks. It’s a teachable moment. When an employee clicks a simulated link, they're immediately taken to a page that gently explains the specific red flags they missed. That hands-on "aha!" moment is more powerful than any textbook lesson.
Running these simulations transforms an abstract threat into a tangible experience. It’s a safe way to fail, providing a crucial learning opportunity without any of the real-world consequences.
The data backs this up. The 2025 Phishing by Industry Benchmark Report found that companies running monthly simulations saw their click-through rates plummet by up to 70%. Even better, organizations that pair these tests with ongoing training report a 50% drop in successful phishing attacks in just six months. For a closer look at the data, you can check out the full report on industry phishing benchmarks.
Fostering a Positive Reporting Environment
Here's the single biggest cultural win you can achieve: create an environment where people feel 100% safe reporting suspicious messages. If employees are afraid they'll be blamed or punished for clicking a link, they'll stay quiet. That silence allows a potential breach to fester and spread.
Leaders need to actively celebrate proactive reporting. When someone forwards a suspicious email to your security team, thank them publicly (without sharing sensitive details, of course). Frame their action as a win for everyone.
This creates a powerful positive feedback loop. It encourages the thought process to be, "Hmm, this looks weird, I'm going to get a second opinion," instead of, "I hope this is legit because I don't want to get in trouble." That simple shift can be the difference between a contained incident and a catastrophic breach, effectively turning every employee into a sensor for your security team.
Common Questions About Phishing Protection
Even with the best game plan, some questions always pop up when you're in the middle of a real-world situation. Knowing how to handle the gray areas is what separates a close call from a costly mistake. This section breaks down some of the most common "what if" scenarios I hear about, giving you clear answers for when you need them most.
Let's get into the nitty-gritty.
First, when a suspicious email lands in your inbox, you have to make a quick call. This simple flowchart is a great mental model for deciding what to do in just a few seconds.
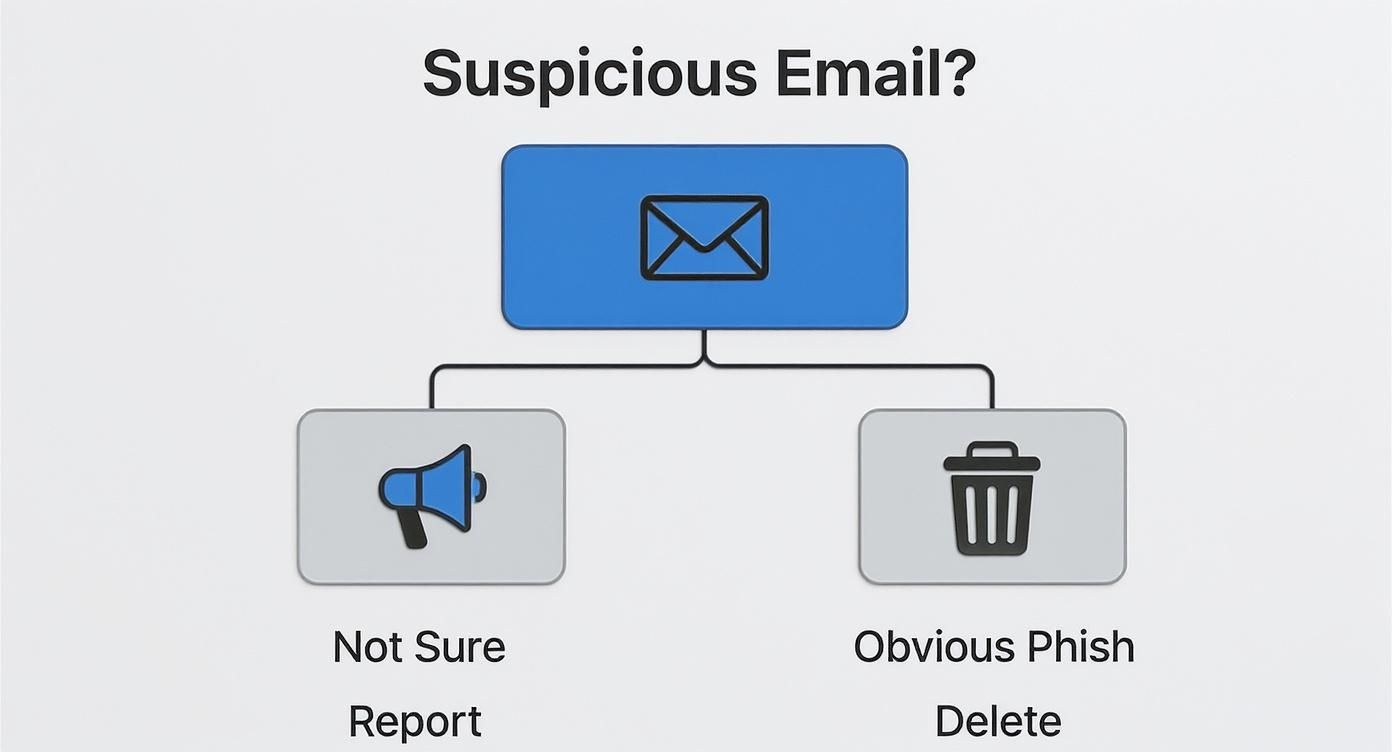
It boils down to a simple rule: when in doubt, report it. Obvious spam? Just delete it.
What Should I Do if I Already Clicked a Phishing Link?
It happens to the best of us. The most important thing is not to panic. If you clicked a link but didn't type in any information, you’re probably okay, but you still need to act fast.
First, kill your internet connection. Disconnect from Wi-Fi or unplug the ethernet cable. This stops any potential malware from phoning home. Then, run a full, deep scan with your antivirus or endpoint security software to catch anything nasty that might have slipped through.
Now, if you did enter your username, password, or financial details, the situation is much more serious. Here’s what you do:
- Change Your Password Immediately. Go directly to the real website—don't even think about using the link from the email again—and change the password for that account.
- Update Every Other Account. If you use that same password anywhere else (a very common habit), you must change it on those accounts, too. A good password manager is a lifesaver here.
- Enable Multi-Factor Authentication (MFA). If you haven't already, turn on MFA for that account right now. It's your single best defense against someone trying to use your stolen login info.
- Watch Your Accounts Like a Hawk. Keep a close eye on your bank statements, crypto balances, and any account activity for unauthorized changes.
Key Insight: The real damage from a phish often isn't instant. Acting quickly can mean the difference between a minor scare and a major security breach. And if it happened on a work device, report it to your IT department immediately.
Is It Safe to Use Public Wi-Fi?
Public Wi-Fi networks in places like coffee shops, airports, and hotels are a minefield. They're notoriously insecure, and attackers on the same network can snoop on your internet traffic in what's called a "man-in-the-middle" attack.
They can see the sites you visit and even trick you into landing on fake login pages. The best advice is to simply avoid logging into sensitive accounts—like your bank or crypto exchange—on public Wi-Fi.
But sometimes, you have no choice. If you absolutely have to use it, make sure you're using a reputable Virtual Private Network (VPN). A VPN encrypts your entire connection, wrapping it in a secure tunnel that makes your data completely unreadable to anyone else lurking on the network.
Will My Antivirus Software Stop All Phishing Attacks?
Think of your antivirus or endpoint protection software as a solid security guard, but not an invincible one. These tools are fantastic at blocking known malware and flagging sketchy websites, giving you an essential layer of protection.
But they can't stop everything.
Many phishing attacks don't use malware at all; they use pure social engineering. A scammer might lead you to a login page that looks perfect but is a complete fake. Your security software might not see anything wrong because there's no malicious code to detect.
It’s like having a great alarm system for your house. It'll alert you if someone smashes a window, but it can't do a thing if you're tricked into opening the front door for a con artist. That’s why your own skepticism is, and always will be, your most powerful defense.
Ready to trade crypto with confidence on a platform that prioritizes your security? Join vTrader for zero-fee trading, advanced tools, and a secure environment designed to protect your assets. Start building your portfolio today at https://www.vtrader.io.

Steve Gregory is a lawyer in the United States who specializes in licensing for cryptocurrency companies and products. Steve began his career as an attorney in 2015 but made the switch to working in cryptocurrency full time shortly after joining the original team at Gemini Trust Company, an early cryptocurrency exchange based in New York City. Steve then joined CEX.io and was able to launch their regulated US-based cryptocurrency. Steve then went on to become the CEO at currency.com when he ran for four years and was able to lead currency.com to being fully acquired in 2025.




