A hardware wallet is a small physical device, kind of like a specialized USB drive, built for one purpose: to give your crypto the highest level of security possible. It keeps your private keys—the secret codes that prove ownership and let you spend your funds—completely offline and isolated. This separation makes your assets practically immune to online hacks, viruses, and theft.
Think of it as a personal, fortified vault for your digital money.
What Is a Hardware Wallet Explained

To really get what a hardware wallet does, let's use an analogy. Imagine your crypto isn’t just data but a set of priceless physical keys to a safe. A software wallet on your phone or PC is like keeping the safe's combination written on a sticky note in your wallet—it’s convenient, sure, but if your wallet gets stolen, you're in big trouble.
Leaving your crypto on an exchange is like handing your safe keys over to a bank for safekeeping. You're trusting them completely, but you never truly hold the keys yourself.
A hardware wallet, on the other hand, is the safe. It's a purpose-built device with a single mission: protect those keys no matter what. It never connects directly to the internet, creating an "air gap" between your private keys and online threats. This physical isolation is the entire foundation of its security.
The Core Principle: Offline Security
The magic of a hardware wallet is that it stores your private keys offline in a protected chip inside the device, called a "secure element." When you want to send crypto, the transaction is prepared on your computer or phone and sent to the hardware wallet for approval.
Crucially, your private keys never leave the device.
The wallet signs the transaction internally and sends only the signed, secure permission slip back to your computer to be broadcast to the network. This clever process ensures your keys are never exposed, even if your computer is riddled with malware.
This rock-solid security model has fueled massive demand. The global hardware wallet market recently hit an estimated USD 474.7 million, showing just how many people are serious about protecting their digital assets.
Hardware Wallet vs Other Wallets at a Glance
Choosing the right wallet comes down to balancing security, convenience, and control. This table breaks down the key differences between the main types of crypto storage.
| Feature | Hardware Wallet | Software Wallet | Exchange Wallet |
|---|---|---|---|
| Private Key Storage | Offline, on the device | Online, on your device | Online, on exchange servers |
| Security Level | Highest | Moderate | Lowest |
| Control Over Funds | Full (self-custody) | Full (self-custody) | None (custodial) |
| Convenience | Less convenient for active trading | Very convenient | Most convenient |
| Best For | Long-term holding, large amounts | Frequent use, smaller amounts | Active trading, beginners |
Ultimately, hardware wallets offer the gold standard for anyone who prioritizes security and wants to eliminate third-party risk.
Who Needs a Hardware Wallet?
You don't have to be a tech wizard to use one. A hardware wallet is an essential tool for just about anyone serious about their crypto, including:
- Long-Term Investors ("HODLers"): Perfect for anyone holding crypto they don’t plan on touching for a while.
- Security-First Users: For those who want absolute control over their assets without trusting an exchange or third party.
- Anyone Holding What They Can't Afford to Lose: If the value of your crypto is more than the price of a wallet (typically $60-$200), it’s a no-brainer investment in your own peace of mind.
By taking custody of your own keys, you’re embracing the core philosophy of crypto: becoming your own bank. For a deeper dive into crypto security and market principles, our VTrader Academy has plenty of resources to get you up to speed.
How Hardware Wallets Keep Your Crypto Safe
So, how does a little USB-like device actually protect your digital assets? Think of a hardware wallet as a tiny, dedicated security guard for your crypto. Its one and only job is to handle your most sensitive information—your private key—in a hostile environment (the internet) without ever letting it out of its sight.
When you decide to send some crypto, the transaction starts on your computer or phone. But the most important part, the final approval, doesn't happen there. Instead, the transaction data is sent over to your hardware wallet for the final signature. This is where the real security kicks in.
Your private keys never, ever leave the physical device. The wallet signs the transaction internally, completely offline and shielded from your potentially compromised computer. It then sends back the signed permission, and only the signed permission. Your keys are never exposed to your PC, which could be crawling with malware or spyware.
The Role of the Secure Element
At the very core of a hardware wallet's defense is a special microchip called a secure element. This isn't just any old chip; it's the same kind of hardened tech you'd find in a modern passport or a high-security credit card. It's essentially a tiny, impenetrable vault built specifically to guard your private keys.
This specialized chip is designed to resist both digital hacks and physical tampering. It creates a completely isolated bubble where all the critical operations, like signing a transaction, happen safely. Even if a scammer took complete control of your laptop, they still couldn't pull the keys out of the wallet's secure element.
Key Takeaway: The secure element is where your private keys are born, live, and do their work. They are never exposed to the vulnerabilities of your main computer or smartphone.
This single design feature makes your crypto virtually immune to the most common online attacks. It’s built to shut down threats like phishing attacks, where scammers try to trick you into giving up your credentials. Since you have to physically approve the transaction, a malicious link by itself is completely useless.
Physical Verification on a Trusted Screen
Another brilliant layer of security is the device’s own screen and buttons. A popular trick hackers use is to display one address on your computer screen while secretly swapping it for their own in the actual transaction data. It’s a classic bait-and-switch.
If you were just using a software wallet on your PC, you might approve that fraudulent transaction without a second thought.
A hardware wallet totally defeats this trick by having its own trusted display. Before you sign off on anything, the wallet shows you the raw, unchangeable transaction details right on its own little screen. You get to verify:
- The Recipient's Address: Is this really the address you want to send funds to?
- The Transaction Amount: Are you sending the right amount? No extra zeros?
- Network Fees: You’ll also see the exact network or gas fees for your final review.
This simple check guarantees that what you see is what you sign. Since the hardware wallet is a separate device, malware on your computer has no way to alter what’s shown on its screen.
The Final Step: Manual Confirmation
The last line of defense is you. Nothing happens without your direct, physical approval. After you’ve double-checked the details on the trusted screen, you have to physically press the buttons on the device to confirm or reject the transaction.
That manual button-press is the final go-ahead. It’s a simple but incredibly effective security measure that proves the real owner is present and giving explicit consent. This creates a nearly foolproof barrier against remote hackers. Understanding how your data is handled is key to security, and you can learn about general data protection in our privacy policy.
This combination—offline keys, a trusted display, and physical confirmation—is what creates such a powerful fortress around your digital assets.
Understanding Your Recovery Phrase: The Master Key
If your hardware wallet is the impenetrable vault for your crypto, then your recovery phrase is the one and only master key. This simple string of 12 or 24 randomly generated words is arguably the most critical piece of information you’ll own in the crypto world. It's your ultimate failsafe.
This phrase isn't just another password. It's a direct, human-readable representation of your private keys. If your hardware wallet gets lost, stolen, or completely destroyed, this sequence of words is all you need to restore full access to your funds on a new device. The crypto itself never lives on the wallet—it's on the blockchain—and your recovery phrase is your permanent claim to it.
Key Takeaway: Your hardware wallet is replaceable. Your recovery phrase is not. Protecting it is your single most important job in self-custody. If you lose the phrase, you lose your crypto. Forever.
The Golden Rule: Never Store It Digitally
The number one rule—the one you absolutely cannot break—is to never, ever store your recovery phrase in any digital format.
That means no screenshots, no text files saved to the cloud, no notes app on your phone, and definitely not in a password manager. Any device connected to the internet is a potential attack vector for hackers, and a digitally stored recovery phrase is a sitting duck.
Putting your master key online completely defeats the purpose of having an offline hardware wallet. You're just re-introducing the very risk you tried to eliminate. It’s like buying a top-of-the-line home security system and then leaving the master key under the doormat.
The whole point of a hardware wallet is to keep the signing process—the moment your private key approves a transaction—in a secure, offline bubble. This visual shows you exactly how that works.
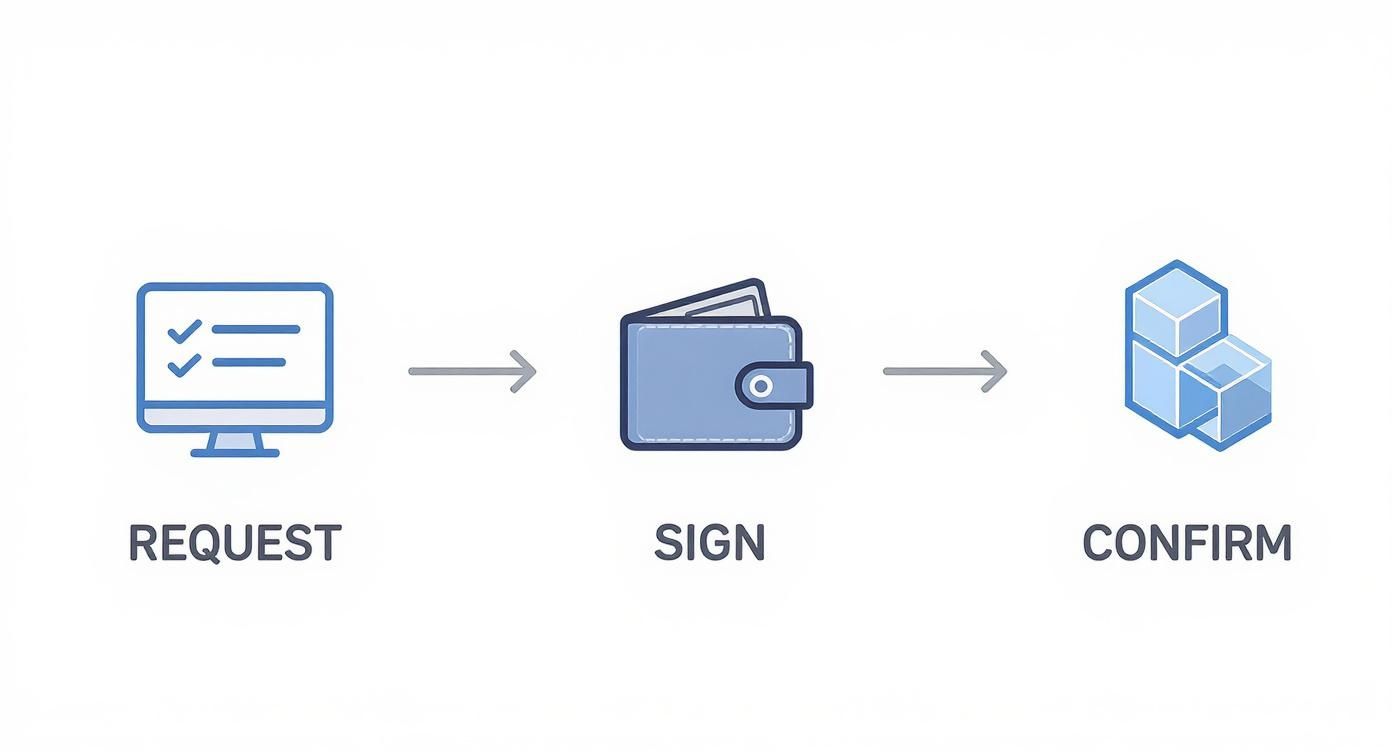
This diagram shows why your backup phrase needs the same "air-gapped" treatment. If your keys never touch the internet, neither should your recovery words.
Best Practices for Securing Your Master Key
Since digital storage is out, you need to think physically. The goal is to create a backup that’s durable, private, and can withstand common disasters. Here are the most effective strategies, from good to best:
- Good (Paper): The simplest method is writing your phrase down on the paper cards that come with your wallet. The key here is to store them in multiple, secure, and geographically separate locations. This protects you if one location is compromised by something like a fire or flood.
- Better (Lamination): A small upgrade, but laminating your paper backups protects them from water damage or fading ink. This boosts their durability against minor spills or humidity.
- Best (Metal): For maximum security, etch your recovery phrase onto a steel or titanium plate. These specialized metal "wallets" are designed to be fireproof, waterproof, and crush-proof, ensuring your master key can survive just about anything.
This push toward robust self-custody isn't just a niche concern; it's a massive market trend. Projections show the hardware wallet market is expected to grow from hundreds of millions to over a billion by the early 2030s. This lines up perfectly with the global crypto user base recently blowing past 400 million people, many of whom are opting for non-custodial solutions to truly own their assets. You can learn more about hardware wallet market findings and see how the industry is shifting toward secure self-storage.
Comparing Your Crypto Storage Options
The best way to truly grasp what a hardware wallet does is to see how it stacks up against the other ways to store your crypto. Each method presents a different trade-off between security, convenience, and your personal control over your assets. The path you choose really dictates how you'll interact with your crypto and the level of risk you're willing to take on.
Think of it like deciding where to keep your cash. You could lock it away in a high-security bank vault (that’s your hardware wallet), carry some in your pocket for daily spending (a software wallet), or just leave it on the counter at a currency exchange shop (an exchange wallet). Each has its place, but they come with wildly different benefits and drawbacks.
Hardware Wallets: The Digital Fortress
As we've covered, a hardware wallet is the undisputed champion of security. It’s a form of cold storage, which is just a fancy way of saying your private keys stay completely offline, totally disconnected from internet-based threats like malware or hackers. This makes it the go-to solution for holding any amount of crypto you can't afford to lose, especially for long-term investments.
The only real trade-off is a minor hit to convenience. To send funds, you have to physically plug in the device and press a button to approve the transaction. But for anyone serious about protecting their assets, this small extra step is a tiny price to pay for genuine peace of mind.
The Bottom Line: Hardware wallets deliver total ownership and Fort Knox-level security. You become your own bank, with all the freedom and responsibility that comes with it.
Software Wallets: The Everyday Billfold
A software wallet (often called a "hot wallet") is simply an app on your computer or phone. You’ve probably heard of popular ones like MetaMask or Trust Wallet. They are incredibly handy for making quick, frequent transactions, interacting with decentralized apps (dApps), and managing smaller balances you plan to use regularly.
Their biggest weakness is their constant connection to the internet. This online exposure makes them a prime target for viruses, keyloggers, and clever phishing attacks that hardware wallets are built to defeat.
- Pros: Super convenient for daily use, simple to set up, and gives you instant access to your funds.
- Cons: Far more vulnerable to online hacks, malware, and what happens if your device gets stolen.
- Best For: Small, "spending" amounts of crypto—think of it as the cash you'd keep in your physical wallet.
Exchange Wallets: The Custodial Account
When you buy crypto on a platform like Coinbase or Binance and just leave it sitting there, you’re using a custodial wallet. This means the exchange holds onto the private keys for you. It’s easily the most straightforward method for newcomers because it feels just like using a regular online banking app.
But that convenience comes with a huge string attached, captured perfectly by the famous crypto mantra: "not your keys, not your coins." You are placing 100% of your trust in the exchange's security. If that exchange gets hacked, goes out of business, or decides to freeze your account, your funds could be gone forever with little to no way of getting them back. It’s a risk that has unfortunately become a reality for many people over the years. To see how different platforms work, you can explore crypto exchanges and their features and find what aligns with your needs.
In-Depth Wallet Comparison: Security vs. Convenience
To really drive the point home, let's lay out the key differences in a simple table. This makes it easy to see the fundamental trade-offs at a glance.
| Category | Hardware Wallets (Cold) | Software Wallets (Hot) | Exchange Wallets (Custodial) |
|---|---|---|---|
| Private Key Control | You hold them offline. | You hold them on your device. | The exchange holds them for you. |
| Security Level | Highest | Moderate | Lowest |
| Main Vulnerability | Physical loss or theft of device/recovery phrase. | Malware, phishing, and device compromise. | Exchange hacks, insolvency, or account freezes. |
| Convenience | Lower; requires physical device for transactions. | High; instant access for frequent use. | Highest; seamless integration with trading. |
| Ideal User | Long-term investors and security-conscious users. | Active traders and dApp users with small balances. | Beginners and active traders who accept the risks. |
In the end, the smartest strategy is often a hybrid one. Many savvy investors keep the vast majority of their portfolio locked down in a hardware wallet while using a software wallet for small, day-to-day transactions. This approach gives you the best of both worlds: rock-solid security for your nest egg and pocket-change convenience for everything else.
How to Choose the Right Hardware Wallet

Picking the right hardware wallet is a huge step toward taking real control of your crypto. With so many different models out there, it’s easy to get lost in the features. But think of it less like buying a new gadget and more like choosing a personal vault. The right one for you depends entirely on what you’re storing and how you plan to manage it.
Don't overcomplicate it. By focusing on a few core criteria—like which assets it supports, its security features, and how easy it is to use—you can find a device that gives you both rock-solid security and everyday convenience.
Evaluate Key Features and Support
First things first: cryptocurrency support. Not every wallet can hold every coin. Before you even think about buying, make a list of the assets you own (or plan to) and double-check that the wallet you’re eyeing is compatible. Most big names support thousands of tokens, but it never hurts to be sure.
Next, think about connectivity and usability. Do you want something you can plug into your computer with a simple USB-C cable? Or would a Bluetooth wallet that syncs with your phone make more sense for you? The physical design is also a big deal. A larger screen makes it way easier to verify transaction addresses, which is a critical step to avoid sending your funds into a black hole.
Finally, consider the firmware. Some wallets can be updated to add new features or patch security holes, while others are fixed from the factory. A non-updatable device offers a certain kind of security—no risk of a malicious update—but an updatable one gives you more flexibility as the crypto world evolves.
The Single Most Important Security Rule
If you only remember one thing from this guide, make it this: always purchase your hardware wallet directly from the manufacturer's official website. Never, ever buy one from a third-party seller on Amazon, eBay, or anywhere else, no matter how tempting the discount.
Why is this a hard-and-fast rule? Because of something called a supply chain attack. Scammers will buy brand-new devices, tamper with the hardware or software to install a backdoor, and then reseal the package to look untouched. An unsuspecting buyer sets it up, moves their crypto over, and wakes up one day to an empty wallet.
Crucial Takeaway: Buying directly from the source is the only way to be certain your device is genuine and hasn't been compromised before it even gets to you. This one simple step wipes out a massive security risk.
The demand for these devices is exploding. The hardware wallet market is projected to skyrocket from around USD 350 million to nearly USD 2.55 billion by 2033. This growth shows just how many people are waking up to the need for secure, self-custody solutions to protect their assets. You can discover more insights about hardware wallet market growth to see where the industry is headed.
Picking the right device and buying it the right way are the cornerstones of self-custody. At vTrader, our goal is to give you the knowledge and tools to navigate this space safely. You can learn more about our mission and how we’re building a secure trading environment for everyone.
Common Hardware Wallet Questions Answered
Even after you get the basic idea behind a hardware wallet, a few practical questions almost always pop up. Let's tackle some of the most common ones to help you feel confident about managing your crypto.
What Happens if I Lose My Hardware Wallet?
This is easily the biggest worry for most people. It’s a scary thought, but the reality is surprisingly reassuring.
Your crypto is completely safe. Remember, your assets are on the blockchain, not stored inside the device. As long as you have that all-important recovery phrase, you can just buy a new wallet—even from a different brand—and restore everything. Your funds will be right there, fully accessible. The lost device is basically a paperweight to whoever finds it, since it’s still protected by your PIN.
Can a Hardware Wallet Get a Virus?
This is another great question. Hardware wallets are specifically engineered to be incredibly resistant to malware. Their operating systems are stripped down to the bare essentials with one single purpose: protecting your private keys.
This minimalist design means they can't run unauthorized software. You could plug your hardware wallet into a computer that's riddled with viruses, and that malware still wouldn't be able to sniff out the private keys from the wallet's secure chip.
Key Insight: Think of a hardware wallet as a secure vault for your keys. It signs transactions in a quarantined digital space, making sure that any malware on your computer can't mess with the transaction details or steal your keys.
Do I Need One for a Small Amount of Crypto?
Finally, people often wonder if a hardware wallet is overkill for a small crypto stash. The honest answer? It comes down to your personal risk tolerance. If you're just playing around with an amount you wouldn't be devastated to lose, a software wallet is probably fine.
But the rule of thumb I always tell people is this: if your crypto is worth more than the cost of a hardware wallet, it's a smart investment. It offers an unmatched level of security for any amount you truly can't afford to lose.
For any other questions, our comprehensive FAQ page offers answers to many common crypto topics. And while hardware wallets are a special case, good digital habits are universal. Knowing how to practice securely wiping data from general electronics before sale is a valuable skill for protecting all your personal information.

Steve Gregory is a lawyer in the United States who specializes in licensing for cryptocurrency companies and products. Steve began his career as an attorney in 2015 but made the switch to working in cryptocurrency full time shortly after joining the original team at Gemini Trust Company, an early cryptocurrency exchange based in New York City. Steve then joined CEX.io and was able to launch their regulated US-based cryptocurrency. Steve then went on to become the CEO at currency.com when he ran for four years and was able to lead currency.com to being fully acquired in 2025.




